Author: Joseph Jachimiec, Security Administrator
Yogi Berra once said, “Okay you guys, pair up in threes… and talk about information security!”
Okay, I added the part about information security. But he still said “pair up in threes,” which is a brilliant Yogi-ism…
Taking his advice to heart, I paired up my knowledge about InfoSec and came up with three things to look for in a secure print partner. Play ball!
1. A Maturing Information Security Program
Your print partner must have an information security program, period.
Bonus points if they have a “maturing” InfoSec program. This means the program (by design) develops and improves over time, guided by business and customer needs. Sprinkle in leadership commitment, reliable frameworks, and awareness training, and you’re off to a good start.
Sounds simple, but it’s not. Consider the following…
Leadership Commitment
A robust information security program starts from the top down. It must have the full support of the CEO and company leadership with a clear security commitment shown to employees, stakeholders, vendors, and customers.
Controls
As discussed in my previous article, a well-designed InfoSec program encompasses administrative, physical, and technical controls.
For administrative controls, think policies and documentation. For physical controls, think door locks, cameras, and key cards. And for technical controls, think firewalls and encryption. Make sure there are policies, standards, procedures, and guidelines in each of these areas.
Frameworks & Training
Ask if they built the program on a well-known cybersecurity framework like the NIST Cybersecurity Framework, CIS Controls, or ISO/IEC 27001:2013.
Also, make sure the print vendor has a diverse security awareness training program for its employees. More about this later.
2. Independent Third-Party Security Audits
Okay, your potential print partner has an information security program. They’ve told you they segment their networks, scan for vulnerabilities (and patch them), and have full documentation and policies.
Do you take their word for it? Or do you, as the Russian proverb goes, trust but verify?
I think you know the answer. But how do you verify? It’s time-consuming and expensive to fly your security auditors out. However, due diligence is a must.
That’s where independent third-party security audits come in. Trained, unbiased auditors perform these evaluations. And in most cases, compliance obligations require third-party validation.
So ask about the third party reports and certifications that confirm your potential print partner is meeting their InfoSec duties. Make sure they’re following industry standards, using best practices, and protecting your data with proven methods.
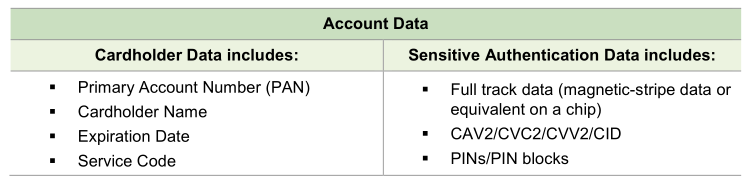
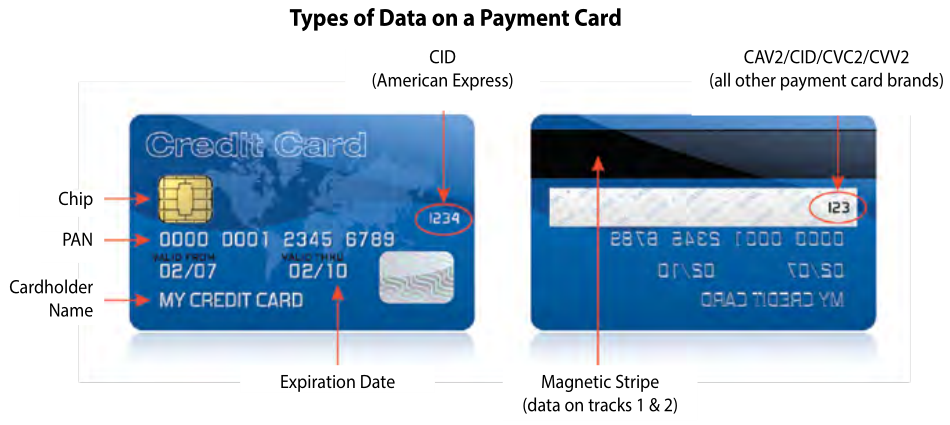
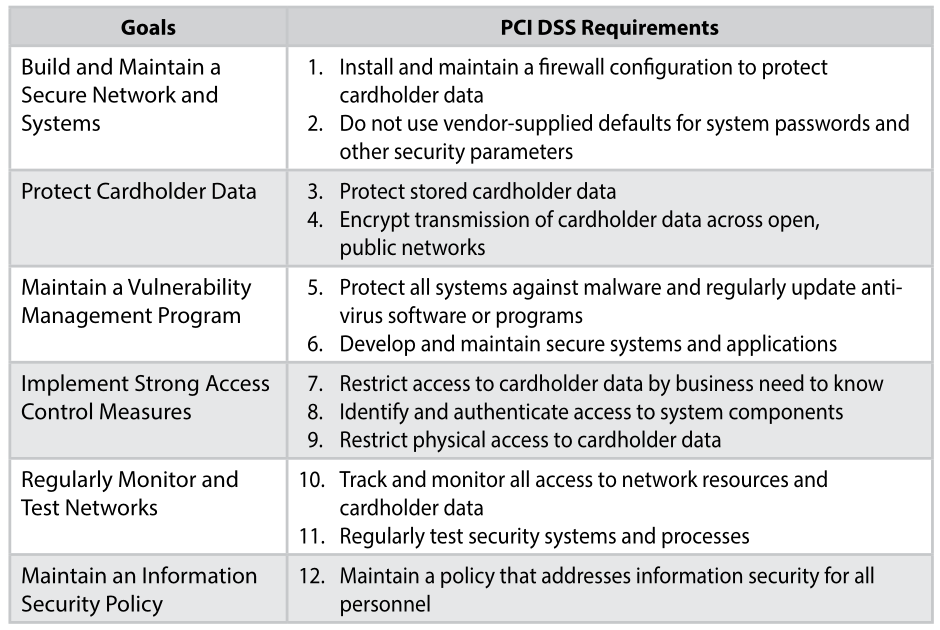
For instance, what’s their S2SCORE? Do they have an AICPA SSAE 18 SOC 2 report? If they process credit cardholder data, are they PCI DSS compliant? If you’re in the healthcare field, is the print vendor HIPAA compliant?
Besides independent audits, does your potential partner have a track record of fixing security gaps? Do they have a history of remediating and improving any security findings the inspections uncover? Or do they strike out?
3. Security Awareness Training Program
I mentioned awareness training above, but it’s so important that I’m calling it out in this separate section.
Someone once said that humans are the weakest link in the security chain (no offense if you’re human). All this means is we’re emotional, and thus easy prey for social engineering trickery.
A robust training program covers a few different bases here. First, it shines a spotlight on the threat of social engineering and teaches ways to identify it when something doesn’t seem right.
It’s not about paranoia; it’s about awareness. It’s about thinking before divulging information, clicking on a strange email link, or plugging in that USB thumb drive.
The security awareness program should use different media like email training, newsletters, video, and even live training. Is the training spread out over different time frames like weekly, monthly, and yearly?
Phishing Tests
To further combat social engineering and ransomware, make sure the vendor’s awareness training program includes email phishing tests and remediation training for anyone who takes the bait.
Policy Acknowledgments
And don’t forget about the print vendor’s security policies. All employees must be aware the information security policies exist, what those policies cover, and where to access those policies for further reference. Annual acknowledgment of security policy training is ideal.
Bonus: look to see if the print vendor cares about its employee’s digital safety outside of work. Security training for their family and home life is a welcome addition.
Conclusion
When evaluating a potential secure print partner, look for telltale signs the print provider cares about your data security. Ask them to prove it.
At the very least, look for:
- A reliable information security program
- Third-party assessments
- A security training program that’s proactive about educating its employees.
Is there more to consider? Sure, but don’t get overwhelmed. Start with these basics, and you’ll go a long way toward protecting your data with your trusted print vendor.
If you’re looking for a secure print partner, contact us today. We’ll show you how Nahan meets all these criteria and more.
Joseph Jachimiec is a security, IT, and marketing professional. As the Security Administrator at Nahan, he heads up our information security program and is the go-to guy for our customer/third-party security audits and PCI, SOC 2, and HIPAA compliance initiatives. In his spare time, he dreams about what it would be like to have more spare time.
Image by Paul Brennan from Pixabay