Data privacy is a looming concern for consumers and thus securing sensitive data should be paramount for direct mail marketers. Data breaches can have severe repercussions, such as financial loss, identity theft, reputational damage, and legal consequences. All of which can be prevented by implementing strict security measures.
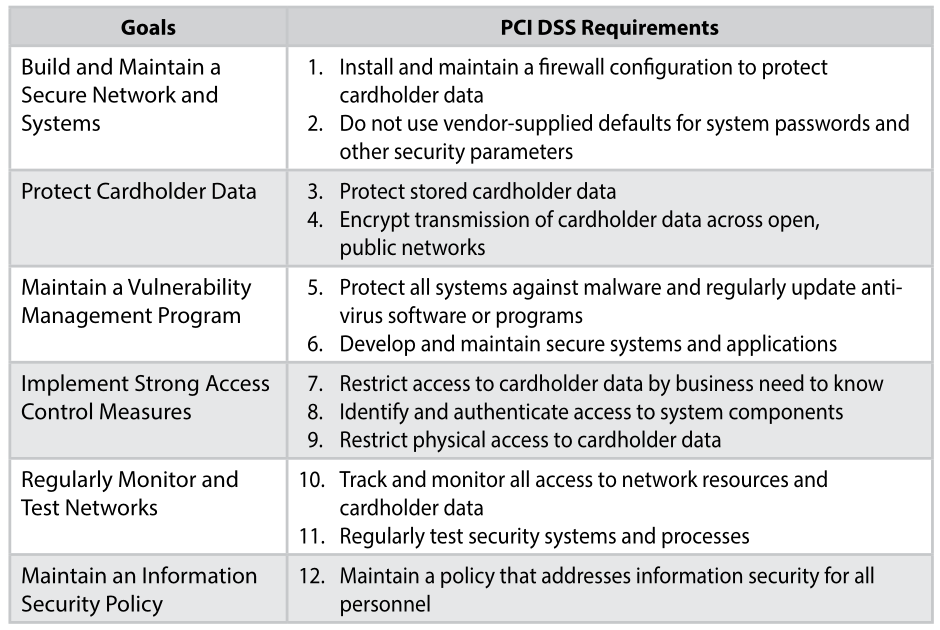
As a leader in direct mail marketing, we adhere to industry best practices and prioritize robust data security measures that enable us to offer personalized direct mail campaigns while respecting privacy and maintaining trust. Nahan maintains compliance certifications like PCI DSS Level 2, AICPA SSAE18 SOC2 Type 2 + HITRUST CSF compliance certifications. We also engage third-party auditors to conduct security audits, penetration tests, and risk assessments to validate our security measures and identify areas for improvement.
It’s important that marketers understand the risks, impacts, and regulatory requirements associated with direct mail campaigns, and how Nahan employs key security measures in response. Let’s dive in!
Importance of Protecting Sensitive Customer Data in Direct Mail Campaigns

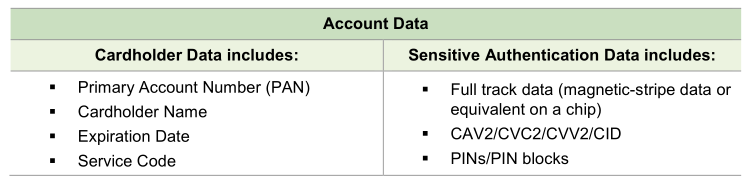
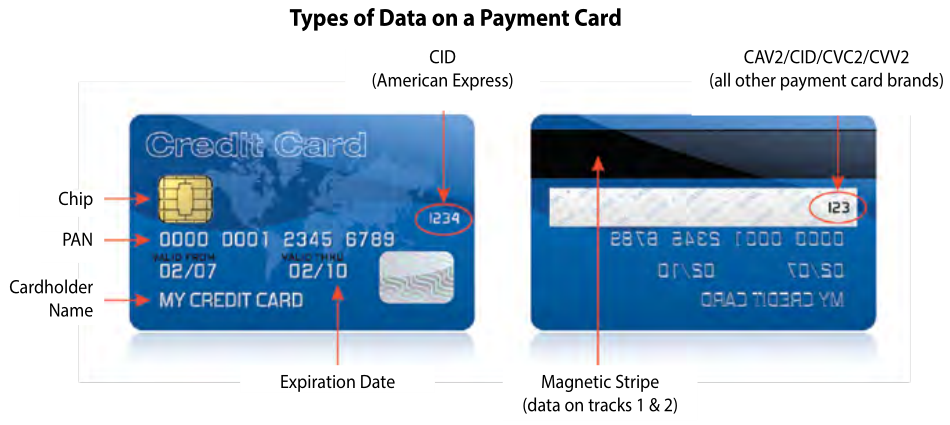
In today’s digital age, where data breaches and privacy concerns are prevalent, protecting sensitive customer data is of utmost importance in direct mail campaigns. Direct mail involves the collection, storage, and processing of customer information, typically names and addresses but can sometimes include purchase history and potentially other sensitive information. Safeguarding this sensitive customer data should be a top priority for businesses engaging in direct mail marketing. It is essential that direct mail providers implement robust security measures to ensure the confidentiality, integrity, and availability of this data.
Common Security Threats and Solutions
When it comes to direct mail campaigns, several common threats pose risks to the security of sensitive customer data. Understanding these threats is essential for implementing effective security measures.
Threat: Data Interception and Breaches
During the transmission of customer data, interception by malicious actors can occur, compromising the confidentiality of the information. Intercepted data can be exploited for identity theft, fraud, or other malicious activities.
Nahan’s Response: Robust Data Protection
Data protection is paramount at Nahan.

Nahan’s robust information security program includes having SOC 2 Type 2 + HITRUST and PCI DSS Level 2 certifications, ensuring comprehensive data governance and privacy protection. We continually monitor our systems and data to detect suspicious activity to stop that activity before it comes a security incident. In the event of a security incident, our incident response team follows a predefined process that includes containment, investigation, mitigation, and recovery. We regularly exercise our incident response to improve our response times and capabilities.
Nahan emphasizes continuous improvement and ongoing training. Regular security training tips and tricks email, training campaigns and other notifications raise employee awareness about data protection best practices and emerging threats
Threat: Unauthorized Access
Unauthorized individuals gaining access to customer data can lead to misuse or theft of sensitive information. This can occur through physical breaches, such as theft of mail or documents, or through cyberattacks targeting electronic systems.
Nahan’s Response: Access Control and Authentication
Segmented, role-based and need-to-know access control limits unauthorized access to sensitive data. Multifactor authentication adds a necessary layer of security, requiring multiple factors of authentication. We also promote a security-conscious workforce through regular employee training related to authentication, password security and phishing.
Nahan implements physical security measures, including access control systems, video surveillance, and equipment protection measures like fire suppression systems and uninterruptible power supply (UPS), to protect premises and sensitive equipment.
Threat: Disaster
There is always the risk of the unthinkable happening, such as cyber-attacks, natural disasters, power outages, and equipment failure, among other disasters. Organizations of all sizes generate a large amount of data, with much of it being extremely important to daily operations.
Nahan’s Response: Disaster Recovery and Business Continuity Planning
We have established a comprehensive Disaster Recovery Plan outlining procedures and protocols for responding to disruptions. Regular testing and refinement ensure its effectiveness, preparing Nahan to handle any unforeseen disruptions effectively.
Secure Direct Mailing Partner

What we’ve learned through seeing various organizations not keep up with information security demand is that it is crucial to work with a partner who can match or exceed your information security requirements. Work with a partner you can trust. We here at Nahan are ready to be that partner because not only will we be able to provide you with an outstanding Nahan experience, but we will also continually work diligently to keep your data safe and secure and continuously improve to keep up with the ever-evolving threat landscape.
By prioritizing information security, Nahan ensures the highest level of protection for sensitive customer data in direct mail campaigns. Our commitment to information security enables our clients to have confidence that Nahan will ensure the integrity and confidentiality of their information throughout the direct mail process.